Gluu
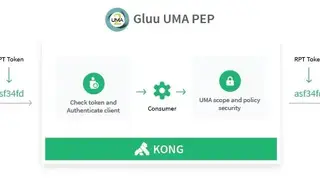
Gluu is the server distribution of the open-source identity components, which are integrated together and deliver as a stable product, making you build an innovative identity platform. To secure your digital identity perimeter, it permits you to horizontally scale both web or persistence resources as needed to achieve the level of burstiness. It persuades you to create special audit logs, implement advanced authentication workflows, add special data into OAuth access tokens, and many others.
Through its advanced Cybersecurity posture, it utilizes modern adaptive authentication techniques, enabling you to stop hackers before they get into your system. With the help of its digital transformation solution, it ensures you to build next-generation e-services that improve the efficiency of operations.
Gluu Alternatives
#1 Okta Identity Cloud
Okta Identity Cloud is a neutral platform that pairs people with the appropriate technology at the proper time. It provides Workforce Identity that includes multiple tools to enable businesses to secure their partners, employees, and contractors. They can maximize productivity while maintaining complete security, prevent data breaches, reduce expenses & promote innovation, and adopt cloud-based technology without facing technical issues.
The platform also offers businesses identity for multiple workforce use cases. It provides secure authentication for your customers and workforce. Other than that, it offers Universal Directory, Advanced Server Access, Lifecycle Management, Access Gateway, and API Access Management. Another product offered by the platform is Customer Identity that lets you add authentication into any app. You can smoothly transition into the API economy, protect customer accounts and block attempts from attackers, retire outdated identities & switch to modern apps, implement secure logins to restrict fraudsters and increase the satisfaction of customers with secure experiences.
Okta Identity Cloud makes it easy to solve all prevailing issues regarding customer identity and use cases. For this purpose, it offers several solutions that include B2B Integration, User Management, Authentication, Access Gateway, API Access management, and Lifecycle Management.
#2 Avatier
Avatier is an industry-leading provider of Identity Management and SSO used by businesses to make their workforce and IT department secure, agile, and compliant. The offered products are fully compatible with modern cloud platforms and on all apps and devices. Furthermore, it takes little time to deploy, usually 14 days or less. It follows a Bring Your Directory (BYOD) approach, enabling you to store identity information in your organization (on-premise) while transferring identity solutions in the cloud.
Avatier offers Passwordless SSO & IGA to help you build frictionless authentication for all apps used across the organization. One main benefit of this feature is that it enhances protection for identity governance and administration. The platform provides powerful REST APIs that the workforce can utilize to offer secure services to customers, increasing their confidence in your business.
Organizations can subscribe to Avatier to reduce expenses and use modern technology ready for deployment on all cloud platforms or On-Premise. They can remove complications by using their current directory for administration and security. The platform increases protection by providing passwordless authentication and allows companies to manage multiple apps simultaneously.
#3 Curity
Curity joins API and Identity security to enable businesses to offer better protection to users accessing websites, digital services, and apps. It provides a secure authentication service that firms can configure to match their requirements. You can increase Trust for access control using customizable tokens and easily manage every user through standardized SCIM API.
Curity uses modern architecture to tackle the current identity structure and deal with future problems with great ease. It follows the separation of concerns in which each module is in charge of dealing with the encountered problem, resulting in enhanced security and true scalability. The architecture is divided into three layers named Standards & Integrations, Configuration and Cluster, and Deployment. The first layer helps you offer consolidated user authentication for all your deployed apps and digital services, enabling server applications to utilize shared APIs.
Configuration and Cluster includes a full-fledged CLI for automation and Web UI that can be set up quickly by reading the provided guides. Curity is ready for deployment on multiple platforms, including Kubernetes, Docker, Microsoft Azure, and Amazon Web Services.
#4 ForgeRock Identity Management
ForgeRock Identity Management enables businesses to deliver seamless experiences for employees and customers. It empowers organizations to manage several types of identities in a single deployment, including employees, collaborators, and customers. The data model is highly extensible and allows you to change the properties of objects, attributes, and schemes, as well as the dependencies between each. The platform is fully capable of managing tens of thousands of transactions per second and, if need be, can extend support to billions of identities.
ForgeRock Identity Management is built to ensure that businesses won’t face downtime during maintenance operations, system crash, service upgrade, and network outages. This allows you to provide maximum coverage and boost customer satisfaction. The platform gives complete flexibility in picking deployment options.
By purchasing a single license, you can obtain multiple cloud environments, including development, testing, and production. It won’t charge extra fees for additional storage. It also provides DevOps tools so your IT staff won’t have to spend countless hours building their own tools. This allows developers to concentrate their efforts on fulfilling their objectives.
#5 Saviynt
Saviynt is a market-leading platform trusted by popular brands to combine identity and increase security & compliance. It provides multiple tools to help organizations overcome their Identity & Security challenges. You can ensure the least privilege without affecting the productivity of your workforce and regularly track controls to fulfill compliance objectives. It allows you to upgrade outdated IGA & PAM to enable speed, security, and agility to align with business goals.
Saviynt makes it easy to protect access across your multi-cloud environments and avoid potential data breaches resulting from contractor/vendor access. It allows you to enhance security by adopting just enough access and make better decisions through predictive analytics. The platform aims to secure your application data, remove weaknesses, and ensure uninterrupted access. For this purpose, it complies with several standards including, FedRAMP Moderate, SOC 1 Type II Audit Report, SOC 2 Type II Audit Report, ISO 27001:2013, and ISO 2707:2015.
#6 SecureAuth
SecureAuth enables businesses to secure all people using their digital products. It offers highly secure authentication methods for all your deployed apps and services and makes it easy for you to deploy Cloud IAM across your organization at full speed. The platform offers adaptive authentication, Multi-factor Authentication, and passwordless Organisation to prevent breaches and unauthenticated logins.
SecureAuth provides a web and mobile SSSO portal to allow everyone to access their dashboards from anywhere, anytime. It also offers password resets to help your workforce to get a new password to access their account. Other features include device enrollment and profile updates to maximize productivity and reduce support expenses.
The platform helps you switch from username and password to scanning device, address, and IP to be able to judge the intent of the person requesting access. Login Security can be strengthened by utilizing a plug-and-play MFA layer to your current IT ecosystem without negatively impacting user activity. Synchronize available directories such as SQL, AD, and enable login through Desktop SSO,
#7 RSA Identity and Access Management
RSA Identity and Access Management is an all-in-one solution that allows businesses to diminish identity risk and maintain compliance without disrupting user productivity. It delivers proper access to users and validates their credentials using modern technology. It can connect to any resource within the organization or on the cloud platform. With the help of the solution, you can enhance the protection of users and connect them to the right application at the right time.
The platform removes complexities in authentication and credential management, resulting in a reduction in operational costs. It follows a risk-based approach, matching the user’s identity with the record in the database to ensure only privileged users can connect to the service. It empowers the workforce and partners to achieve more without negatively impacting security or facility. RSA Identity and Access Management offer flexibility to your user base in selecting their desired authentication method.
#8 Spybot Identity Monitor
Spybot Identity Monitor is a flexible threat detecting software that provides you tools to check whether your information is in the hand of the hacker or not. The platform functioned on advanced technology that keeps you notified about the leakage of your data and information. Once you know your data is leaked, then you can instantly change your password.
The software has an easy installation setup and is simple to use with an elegant interface, and all you need to provide your email address, and you can see all details of the breach of your data. You can add accounts as many you want and get information about all your emails. Spybot identity Monitor is permitting a blazing service that provides you an overview of breaches and known sources for the set of an account.